Private Information Exchange
Cantata Health’s Private Information Exchange (PIE) enables organizations to exchange client health data from their clinical and financial management systems internally and externally, ensuring compliance and data accuracy.
Key Features
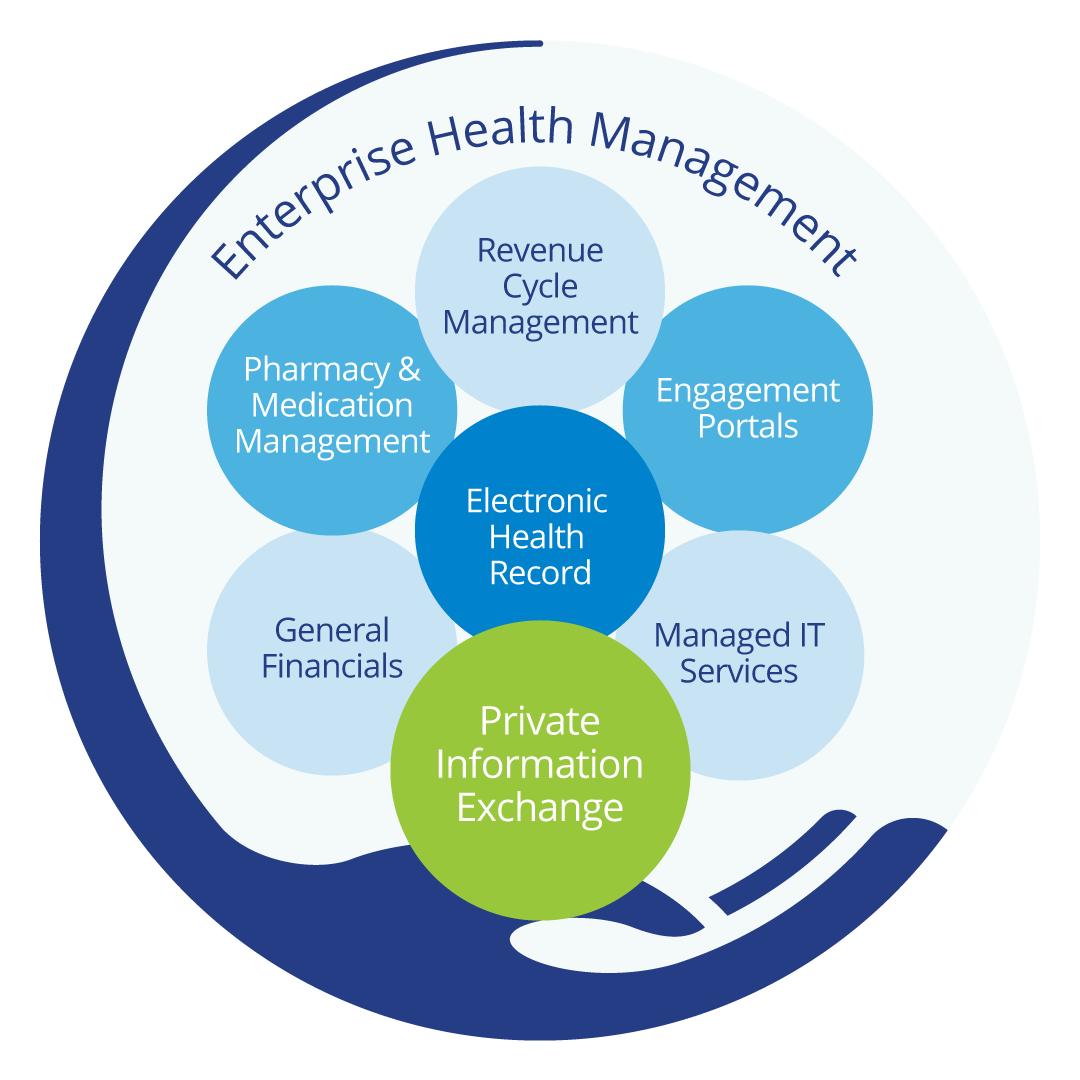
PIE Supports:
- Secure Data Sharing across other hospitals, agencies, private practices, ACOs, and other information exchanges.
- Robust Analytics
- Seamless Communication between clients and providers
- A comprehensive view of an individual’s health record
- Service and Outcome Tracking
- Alerts and real-time event notifications
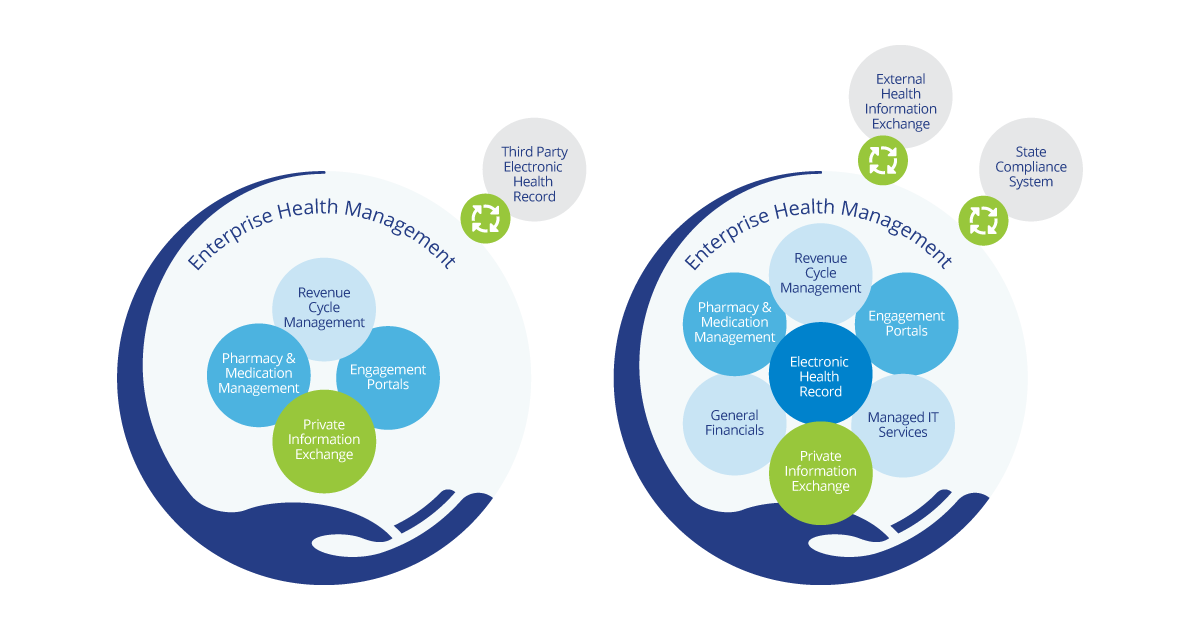
As you can see above, PIE can be configured to meet the unique requirements of your organization. This includes seamless integration with state compliance systems, external information exchanges, third-party systems including Electronic Health Records, Revenue Cycle/Medication Management, Engagement Portals, Lab, Radiology/Imaging, and much more!
Summary
Private health information exchange, or simply Private Information Exchange (PIE), offers an innovative way to facilitate care coordination, connecting providers and stakeholders with secure data exchange. Not only does it streamline existing interfaces for additional connections at lower expenses, but its powerful configuration tools give healthcare providers the power to easily customize their large-scale implementations. PIE is a comprehensive solution capable of scaling up as your needs evolve – truly giving you control over how you manage care coordination in your day-to-day operations.
Our platform is designed to empower organizations of all sizes by providing secure, reliable and easy-to-use bidirectional file transfer solutions. Our centralized data repository further eases collaboration between agencies, providers and their own external tools – creating a holistic approach that goes beyond healthcare needs alone!
